Manage Project Security
Introduction
Security can be set to control access to:
-
projects
-
collections
-
networks.
Security can also be set for Structured Data Source Connections. See Define a Data Source Connection.
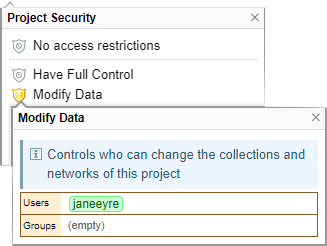
Project Security
Primary security control is set at the project level, where you can control who can:
-
access to the project
-
have full control over the project
-
modify the collections and networks in a project
-
modify the configurations in a project.
The secondary security control is restricting access to an individual collection or network in addition to the above controls.
Types of Security
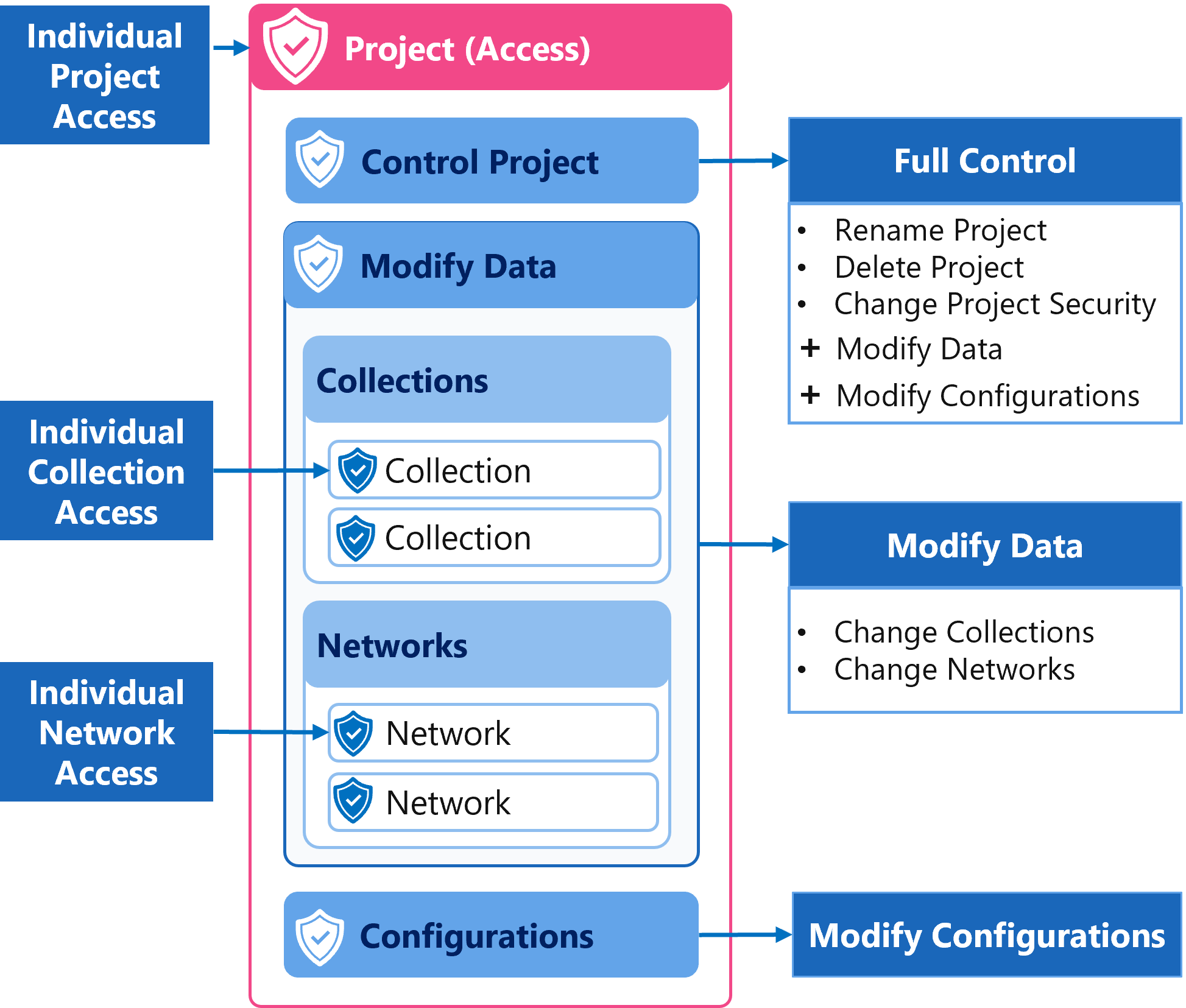
The table below summarises the different project security settings.
|
Security Setting |
Project |
Individual |
Individual |
|
|---|---|---|---|---|
|
Access |
|
|
|
|
| Full Control Security Settings, Rename, Delete, plus Modify Data and Modify Configurations |
|
|||
|
Modify Data View Configurations User requires an Analyst role to modify Networks. |
|
|||
|
Modify Configurations User requires a Configurer role to modify configurations. |
|
Security Summary Diagram
Security Icons
Security icons are shown to indicate the users level of access.
The icons are located next to projects, collections, networks and security settings.
|
Icon |
Status |
|---|---|
|
|
Unrestricted Can be accessed by anyone |
|
|
Restricted Can be accessed by the current user |
|
|
Insufficient Privileges Can not be accessed by the current user User cannot view the security applied. |
Security Model
Sintelix comes with a Default Security Model allowing security settings to be assigned to users or groups.
Administrators can create a Customised Security Model if required to set different security standards.
See Customise the Security Model for more information.
Administrator Access
In the Sintelix Default Security Model there are no restrictions on administrators accessing projects, collections, networks or configurations.
If access has been restricted, the ![]() Restricted icon is shown and the administrator has access.
Restricted icon is shown and the administrator has access.
The administrator will not see the ![]() Insufficient Privileges icon.
Insufficient Privileges icon.
View Security Settings
Clicking on the security icon will show the restrictions applied.
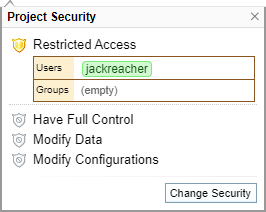
Example 1
In the diagram below, this project is restricted to one user.
Example 2
In the diagram below, this project is not restricted however only one user can modify the data.